This enterprise-level SFTP Server is the solution that, unlike standard FTP, encrypts both commands and data. This prevents your company’s passwords and sensitive information from being transmitted in plain text for anyone to read online. A higher level of security for you.
Our SFTP Server for Windows supports encryption, key exchange algorithm and customizable MAC. It also includes support for reverse proxy – the “digital doorman” that inspects requests for information and determines if they are valid. This SFTP solution holds a reactive & proactive event system with scripting and integration support.
Our SFTP solution uses Secure Shell (SSH), to create a secure connection when you want to integrate/enable automatic file transfers between systems. SFTP also supports SFTP clients for end users that require secure transactions or automatic connections. It may, for example, be about connecting external workspaces as local drives. This can, if desired, be done in combination with Virtual Private Network (VPN) and a reverse proxy in a demilitarized zone.
SFTP server features #
USER MANAGEMENT – ACTIVE DIRECTORY INTEGRATION
Support for Active Directory including users and security groups coupled with impersonation even when using public/private key authentication.
USER MANAGEMENT – VIRTUAL USER INTEGRATION
Integrate user access control with business systems, databases, or other general purpose user management systems. Still being able to use public/private keys defined in scripts! Avaliable for maxi license and above.
USER MANAGEMENT – ADVANCED SETUP
Support for recursive group memberships, through AD integration or not, with detailed ability to override certain settings “down the chain” for specific users/groups.
INTEGRATION & CUSTOMIZATION – SCRIPTING
Execute scripts, automate processes, integrate with any other system and react to any event including file system changes. Avaliable for maxi license and above.
INTEGRATION & CUSTOMIZATION – STEALTH MODE
Reduce access vectors by running your server in stealth mode to give no indication of what server software is used. Even the low-level SSH server identifier can be customized!
COMPATIBLE
Known to work with all SFTP clients (if you find one that does not work, please tell us!).
ROBUST CONNECTIVITY
Even if clients disconnect abruptly due to shaky line or whatever the service will stay up and transfers can be resumed.
SUPPORT ALL PROTOCOLS v1-6
Full support for the IETF Internet Draft versions 1 through 6.
INTEGRATION & CUSTOMIZATION – SECURITY
Complete control to specify which MAC and Key Exchange algorithms to allow/disallow.
MAC ALGORITHMS
Available MAC algorithms are. HMAC-SHA1, HMAC-SHA1-96, HMAC-MD5, HMAC-MD5-96, NONE, HMAC-RIPEMD160, HMAC-RIPEMD, HMAC-RIPEMD-OPENSSH, HMAC-SHA256, HMAC-SHA256-96, UMAC32, UMAC64, UMAC96, UMAC128, HMAC-SHA2-256, HMAC-SHA2-512, AES128-GCM, AES256-GCM, POLY1305, SHA2-256-ETM, SHA2-512-ETM.
ENCRYPTION ALGORITHMS
Available encryption algorithms are. 3DES, BLOWFISH, TWOFISH256, TWOFISH192, TWOFISH128, AES256, AES192, AES128, SERPENT256, SERPENT192, SERPENT128, ARCFOUR, IDEA, CAST128, NONE, DES, AES128-CTR, AES192-CTR, AES256-CTR, 3DES-CTR, BLOWFISH-CTR, TWOFISH128-CTR, TWOFISH192-CTR, TWOFISH256-CTR, SERPENT128-CTR, SERPENT192-CTR, SERPENT256-CTR, IDEA-CTR, CAST128-CTR, ARCFOUR128, ARCFOUR256, AES128_GCM, AES256_GCM, AES128_GCM-OpenSSH, AES256_GCM-OpenSSH, CHACHA20, CHACHA20-OPENSSH.
KEY EXCHANGE ALGORITHMS
Available key exchange algorithms are. DIFFIE-HELLMAN-GROUP-SHA1, DIFFIE-HELLMAN-GROUP-EXCHANGE-SHA1, DIFFIE-HELLMAN-GROUP14-SHA1, DIFFIE-HELLMAN-GROUP-EXCHANGE-SHA256, RSA1024-SHA1, RSA2048-SHA256, ECDH-SHA2-NISTP256, ECDH-SHA2-NISTP384, ECDH-SHA2-NISTP521, ECDH-SHA2-NISTK163, ECDH-SHA2-NISTP192, ECDH-SHA2-NISTP224, ECDH-SHA2-NISTK233, ECDH-SHA2-NISTB233, ECDH-SHA2-NISTK283, ECDH-SHA2-NISTK409, ECDH-SHA2-NISTB409, ECDH-SHA2-NISTK571, ECDH-SHA2-CURVE25519, CURVE25519, CURVE448, GSS-GROUP-EXCHANGE-SHA1, GSS-GROUP-SHA1, GSS-GROUP14-SHA1.
Reverse Proxy (ProVide Gateway)
ProVide Gateway, is an optional reverse proxy that allow communication with ProVide through DMZ, that safely terminates all connections, and never stores any data in your DMZ. Clients do not connect directly to the server, but instead through the gateway, and in turn the server is located safely in your internal network. External clients connect as usual. ProVide Gateway has been tested and on Windows (version 7, 10, 2016, 2019) and Linux (Ubuntu 16.04.5, 18.04.4 & 20.04 LTS, Centos 8, SUSE Enterprise Server 15 SP2). ProVide Gateway is used on other Linux distributions as well. Requires ProVide Gateway License.
Public/private key authentication #
ProVide is very robust and secure. It can handle public/private keys for authentication – for example a key generator tool like PuTTYGen, that creates pairs of public and private SSH keys. The client keeps the private key secure on the client’s local computer, and distributes the public key to be imported into ProVide. ProVide then associates this public key with the user’s account, and uses it to verify the correct key pair and authenticate the account. ProVide supports any combination of allowing/requiring a specific key, in addition to providing a password or not. You may even specify several public keys.
Or, if you are to manage keys yourself, ProVide can generate a public/private key pair for you.
This can be done by navigating to “Users” -> “Security” in the administration interface and clicking the “Generate Key Pair…” button.

Once generated, the public key will be automatically assigned to the account, and the private key will be made available for download and distribution to the intended recipient.
Using virtual users, it is also possible to generate accounts from for example a database, or any other source. The DocWiki shows a simple example on how to integrate virtual users with a public/private key authentication requirement for SFTP connections.
Taking this further, ProVide can also optionally cache Active Directory account passwords to enable public/private key authentication for domain accounts and even use impersonation – in order to be able to access rights that a certain user has – at the same time. This makes ProVide a one-of-a-kind solution, where you can combine scripting and still have impersonation security.
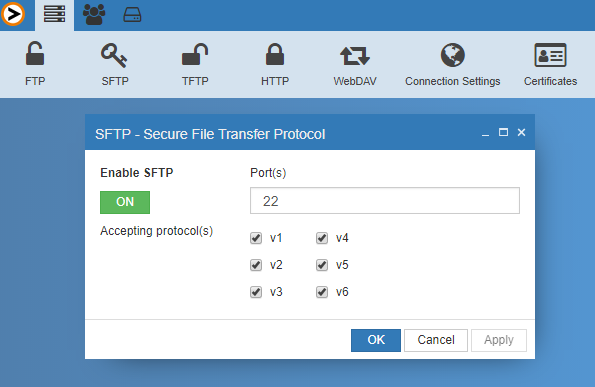
To access the SFTP settings you need to login on the web based Admin interface with an account that has Admin privileges then in the top menu you click on SFTP.
The resources lists all details regarding how to specify MAC and Key Exchange algorithms.






